New to Rust? Grab our free Rust for Beginners eBook Get it free →
Integrating Bot Management Solutions into Application Security Testing

DevSecOps plays a crucial role in safeguarding the modern organization, therefore it seems to reason that managing bots should be one of their many duties. DevSecOps’ fundamental objective is to guarantee that organizations are properly protected against dangerous bots. Bot management is crucial to security and is therefore central to this mission.
What is Bot Management?
You may control which bots have access to your web assets by using an approach called bot management. Bot management techniques aim to spot bot activity, pinpoint the bot’s origin, and ascertain the activity’s nature.
To avoid negative effects on your site’s performance and security, bot management is essential. Malicious bots can overburden servers and prevent or slow down legitimate users if they are given access to your assets. Some bots can also be used to steal system data, credentials, or proprietary assets in addition to scraping your content. Following that, these tools can be employed to phish users, spam content, or organize cyberattacks.
How Does Bot Management Work?
The capabilities and uses of bots by attackers have led to the evolution of bot management solutions. Identifying attacker bots, which are becoming more adept at imitating human users, and separating malevolent from legal bots, which can be crucial for an organization’s daily operations, are the two challenges that modern bot management faces.
Importance of Bot Management in Application Security Testing
Every organization should prioritize bot management as part of its security and operational procedures. Bot management is considered an important part of application security testing, there is no reason to take a risk you don’t have to because the effects of bots can range from minor annoyance to severe income loss. The hazards that bot management can help you avoid are listed below.
Security
Some harmful bots can compromise website security by infecting users with malware, which can result in expensive data breaches and privacy violations. Bots can also intercept sensitive user data being submitted on websites and exploit it to carry out crimes like account takeover attacks and identity fraud.
Distributed denial-of-service (DDoS) attacks
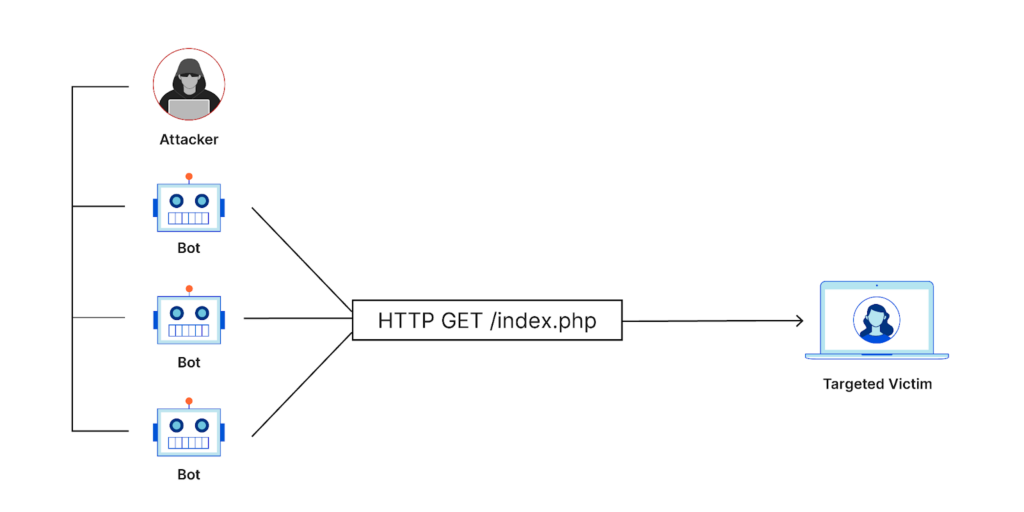
DDoS assaults utilize networks of bots or hijacked devices to flood servers with requests, use all available bandwidth, and overload computing power. Sites, programs, or services can become unavailable as a result. Individual PCs or Internet of Things (IoT) devices may be used in these assaults. Because there are so many IoT devices and they tend to be less secure than workstations or other PCs, their use is growing.
Click Fraud
When visitors click on the adverts, ad-serving websites are paid. Malicious bots can mimic this behavior and click on ads supplied on a page to make it appear as though they are being made by actual people. While this could temporarily increase a website’s revenue, advertising networks have the ability to identify bot clicks, and if they do, they may ban the website and its owner from their network for engaging in click fraud. Finding a means to recognize and block harmful bot traffic is crucial.
Information Gathering
In order to find personal information about users, attackers can use bots to crawl or scan websites, social media platforms, or forums. Attackers can then use this data to carry out phishing attacks, impersonating a trusted source while deceiving users into disclosing sensitive information.
Website Performance
Bots are programs that can flood a website’s servers with hundreds of requests at once. Due to this, websites may take too long to load or cease to exist entirely for actual human users.
Credential Stuffing
Attackers who use bots to automatically attempt lists of stolen or leaked credentials until one is accepted are known as credential stuffing. With the help of these attacks, attackers can enter systems by brute forcing and hijacking user accounts. Users commonly use the same login credentials for various accounts, which makes these assaults successful rather frequently.
Web Exploitation of Secured Content
Bots are used in web scraping attacks to crawl, scan, and retrieve protected assets from websites or storage facilities. These assets could be hidden files, pricing information, logos or branding materials, or product details. eCommerce websites and portals, such as those for ticketing, travel, and online gaming, are particularly susceptible to web scraping.
How Bot Management Can Enhance the Overall Security of Web Applications
Enhance the Customer Experience
The experience that your customers have on your website, mobile app, or other applications may be significantly impacted by bot activity. In fact, even traffic from trustworthy bots can affect how usable your website is by slowing it down and making it more challenging to use.
Keep an Edge over Attackers
Many bot detection tools have an extremely tough time identifying bad bots since they can deftly mimic human behavior. However, if you choose the proper solution, you can make sure that even these bots that try to avoid detection are found and dealt with appropriately. The best defense is the detection and prevention of automated attacks.
Reduce Bot Traffic
It is more crucial than ever for businesses and organizations of all kinds to take safeguards in light of the increase in malicious bot traffic. To safeguard your company and stop malicious bots from causing significant issues, you must use bot detection and bot mitigation solutions.
Conclusion
Companies that offer consumer applications must safeguard their consumers’ online safety, financial security, and data privacy. DevSecOps is necessary to secure clients in any organization seeking to gain a competitive edge through the quick innovation made available by DevOps. This ensures that security keeps up with the rate of releases.
Bot management is one of the duties of DevSecOps that is crucial. DevSecOps brings capabilities to the table that is particularly helpful for protecting against hostile bots and enabling organizations to securely embrace rapid innovation. Bot assaults seriously jeopardize client security.