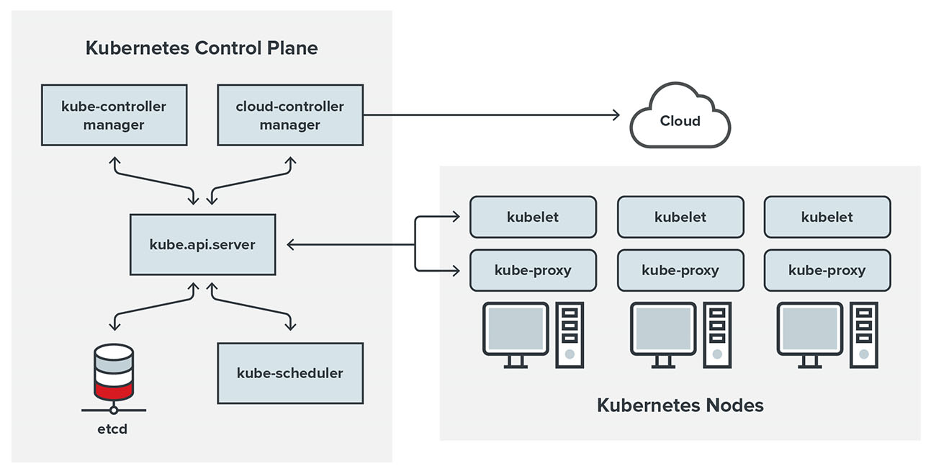
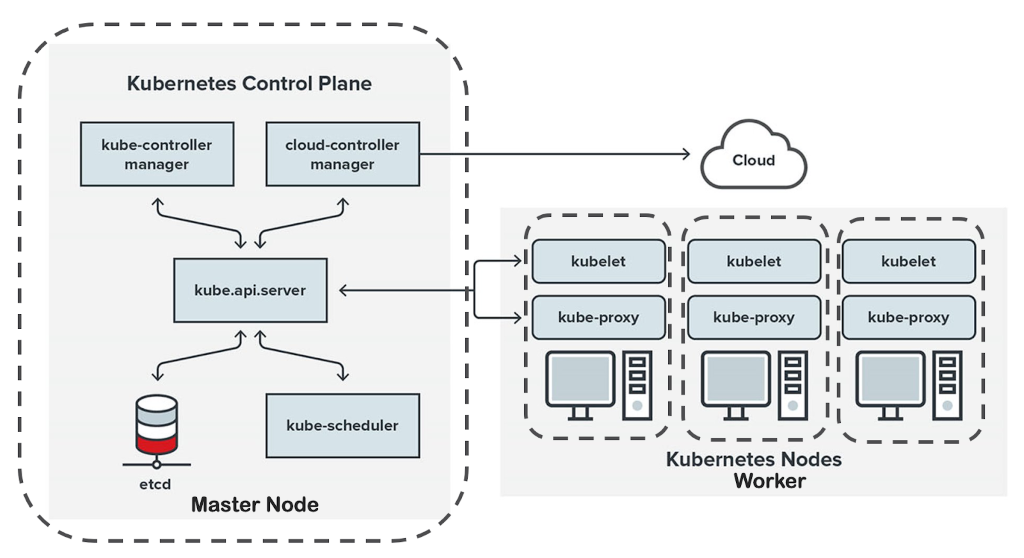
To build and manage microservices, many organizations rely on Kubernetes, a well-known open-source container orchestration technology that is used by many enterprises. To run containerized apps in production while also controlling and scaling them as needed, organizations rely on container orchestration solutions such as Kubernetes.
Using the Kubernetes container orchestration system, you can save time and money by automating a variety of tasks such as deployment, scaling, and overall management of containerized applications. Please keep in mind that if you do not have proper security measures in place, this same instrument may cause significant breaches in your defenses. The simplest of vulnerabilities in one of the containers running inside a pod might compromise the entire node and even the cluster and cause it to crash.
Sealing Kubernetes Apps from Vulnerabilities
It is necessary to employ a variety of ways to safeguard your Kubernetes installation against vulnerabilities. In this article, we will take a look at some of the most fundamental ways.
Continuous Vulnerability Scanning
Containers may have some outdated packages, which may contain some of the vulnerabilities that have since been publicly exposed. The implementation of continuous vulnerability scanning both before and after the construction of a container is therefore crucial.
New vulnerabilities are identified on a daily basis, there is no way to undertake a ‘once-and-for-all’ security assessment approach. As a result, vulnerability scanning is an ongoing process in which images are evaluated on a regular basis and vulnerability scanning is performed to discover flaws that may pose a threat to the information security of the organization.
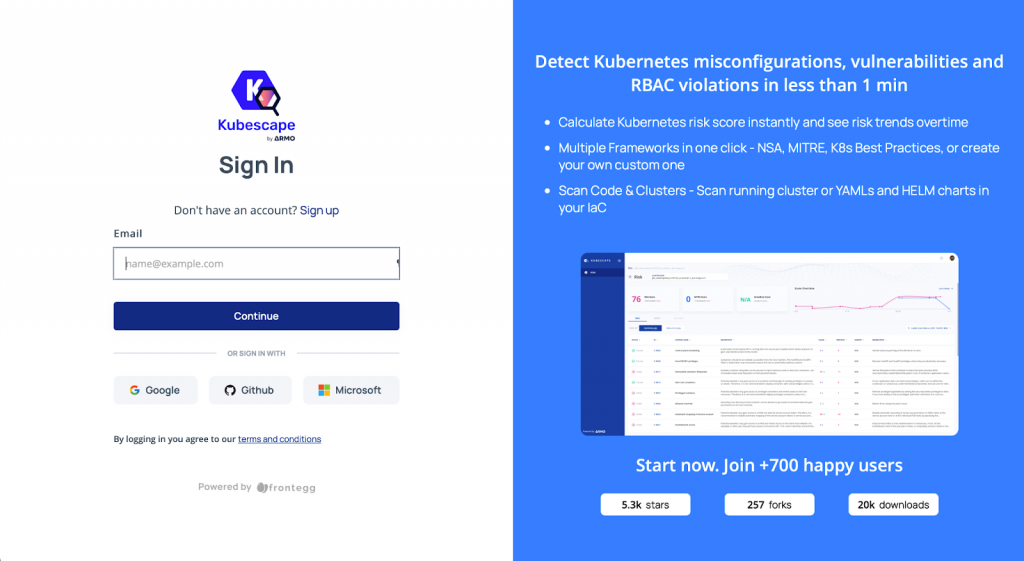
To accomplish this, organizations employ a variety of scanning tools. An example of an open-source tool that I have found particularly useful for this is Kubescape by ARMO, which scans Kubernetes clusters, YAML files, and helm charts during the initial stages of the CI/CD pipelines.
Once the container is deployed, it performs continuous monitoring of the cluster’s posture, vulnerability scanning and remediation, and such. While in production, it performs a wide range of functions, such as offering runtime observability, secret protection, and zero trust network protection. It serves as a one-stop solution for all of your security requirements. To check out Kubescape, you can take a look at it on GitHub.
When creating images or containers, it is critical to do vulnerability scanning on them to identify any vulnerabilities that may exist before deploying them.
Ensuring Only Authorized Images Are Used
Organizations should take precautions to ensure that only authorized images can be allowed to run in their environment. If this is not done, the organization runs the risk of running vulnerable images that may contain vulnerabilities, increasing the likelihood of the organization’s environment being compromised.
It is necessary for organizations to establish private registries that include only approved images in order to ensure that only approved images are utilized in the environment. Once an image has been accepted, it will be added to the private registry, where it will be available for usage.
The continuous integration pipeline should ensure that only approved code is utilized in the production environment for image creation. The organization may be open to attacks if the necessary approval process is not followed.
Regularly Updating the Environment
Every day, new vulnerabilities in various packages and software are discovered and publicly disclosed. Once a security vulnerability in any of the installed images or the packages has been discovered, it should be updated in the source image and its packages before being relaunched in order to reduce the security risk associated with those containers.
At the same time, though, it is necessary to avoid some of the direct update instructions on currently operating containers because it may cause damage to the image-container relationship. But now, with the Kubernetes rolling updates functionality, it is quite simple to upgrade containers. This feature lets you progressively update a running application by incrementally replacing the pods’ resources with the new ones, thereby updating the vulnerable packages.
To avoid having to perform manual commands to update the containers, it is usually recommended that you make use of Kubernetes’ rolling functionality.
Disable Direct Access to Host
Kubernetes provides a variety of connections to nodes including SSH. SSH access to Kubernetes nodes should always be restricted due to the fact that it allows direct access to the host. Restricting SSH access can reduce the risk of unauthorized access to host resources on the cluster. In lieu of this, you can instruct your team to use “kubectl exec”, a command that will provide direct access to the container environment without requiring access to the host.
When using Kubernetes Authorization Plugins to further manage user access to resources, it is possible to disable SSH access from within the cluster. Access control rules can be defined for specific namespaces, containers, and operations, allowing for finer-grained control over access.
Conclusion
Kubernetes makes it possible to quickly and simply launch microservices and can aid in the scaling process. However, because Kubernetes is a very complex technology, it can be difficult to manage it. As a result, it is critical that all the best practices are adhered to in order to protect Kubernetes from vulnerabilities and to ensure the overall security of the cluster.