New to Rust? Grab our free Rust for Beginners eBook Get it free →
Vulnerability Scanning in DevSecOps

As security and privacy concerns have become a major conversation in the IT industry, companies have started to embrace security as a main business discipline. Within this larger topic is the concept of vulnerability scanning. In this article, we will talk about this in the scope of DevSecOps.
DevSecops—Baking Security into the Whole Development Lifecycle
Let us first understand what DevSecOps is. At its simplest, it incorporates security into the whole process of planning, designing, coding, deploying, and releasing software (DevOps).
Traditionally, security has been an afterthought. Many previously felt that security is simply the job of the ‘security guys’. These are people whose only task is looking for holes in the code base, database, or running application. However, because of the prevalence of attacks, security has now become part of the development process.
What is Vulnerability Scanning?
Vulnerability scanning (or more commonly called ‘vuln scan’) is simply performing an automated scanning of a network, codebase, or system to detect any security vulnerability. This is one of the integral aspects of DevSecOps.
This scanning should result in a list of all possible weaknesses in the code being scanned. The end goal is for the organization to be able to remediate the vulnerabilities to prevent any malicious entity from discovering and exploiting them.
What Kind of Vulnerabilities Should You Scan For?
OWASP periodically releases its list of Top 10 vulnerabilities to guide organizations into preventing attacks on their systems and software products. Thus it also protects the users that use these systems and products. In general, though, these vulnerabilities can be categorized into affecting the following aspects of a system.
Network
This type of vulnerability may be found in the firewalls, network layers (TCP/IP), wireless and LAN connections (i.e., insecure access points), and servers. Essentially, it’s more of a hardware and configuration issue.
Operating System
Since company servers also run using certain operating systems, this category involves weaknesses in such operating systems. Attackers may take advantage of (i.e., take over it) and sabotage the entire system.
Process
Examples of this include weak password policies and session management vulnerabilities. An organization’s processes within the whole software development lifecycle should involve security checks before passing through the next stages.
Human
When we deal with vulnerabilities involving humans, we are not just talking about human error (which happens a lot) but also attacks performed physically. For example, when a database administrator wilfully gives their credentials to an external party with the intent of allowing such a party to steal user data or other sensitive information.
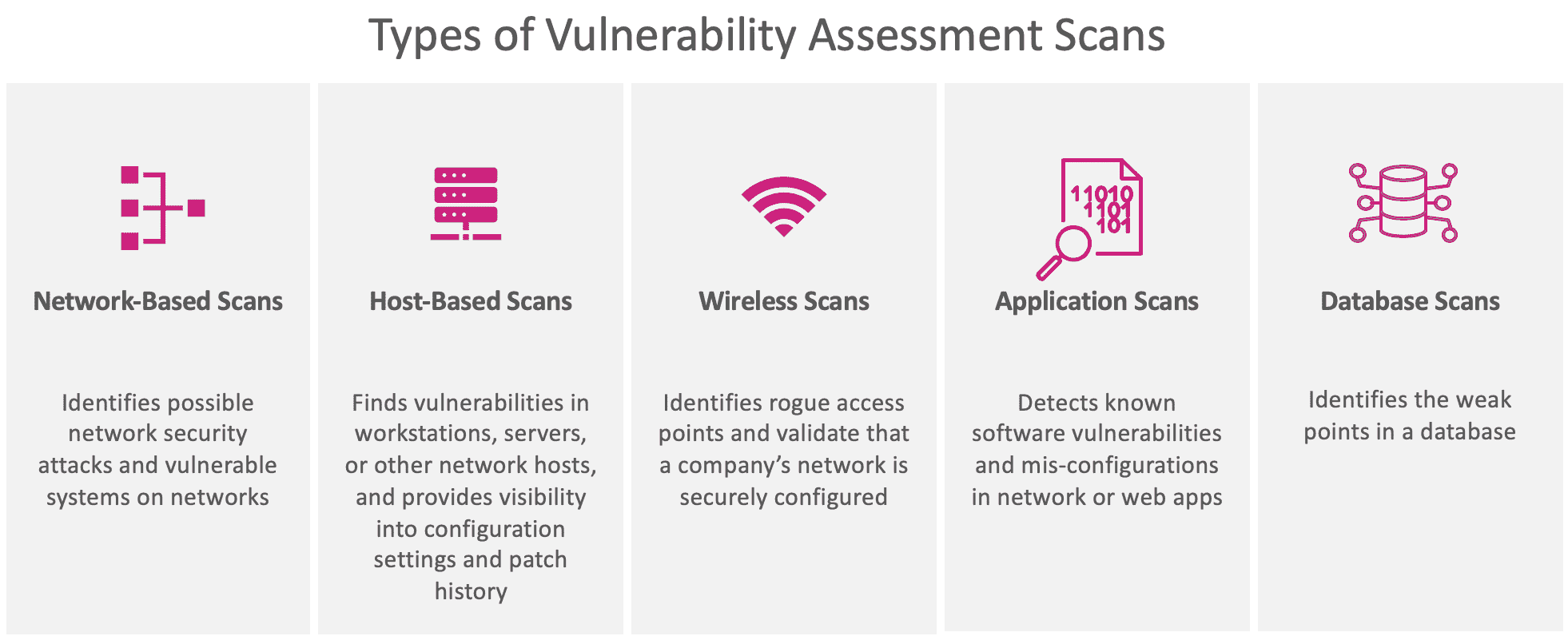
Different Types of Vulnerability Scans
External
External scanning is done on publicly exposed surfaces of the software. This may involve the API endpoints, the website/web pages, ports, networks, and everything else that gives access to users for the application.
Internal
Internal scanning is performed on the company’s own networks, servers, and on the codebase itself. Essentially, should the external scan fail to prevent an intrusion (say, a malicious script gets past external scanners), then the organization should be able to still catch it within the boundaries of its internal system.
Environment
This involves scanning all the environments that the software is being executed on or tested against. Internally, there may be several pre-production environments to scan. It may also involve testing the software on the different devices it will run on (i.e., iOS, Android, desktop).
Conclusion
Vulnerability scanning should be part of a company’s core processes when dealing with software. Neglecting this opens it up to all sorts of troubles down the road.
Why so?
Security vulnerability scanning isn’t just performed by your IT department; it is also done daily by attackers. Attackers are always on the lookout for weak spots in every software. So, why give them the upper hand? Responsible organizations should always have very strong defenses against attacks. Putting vulnerability scanning as an integral part of the process ensures that any vulnerability (at least the critical and high severity ones) can be quickly taken care of.