In the previous article, we studied Blockchain and its history. In this article, we are going to study the core components of Blockchain.
Blockchain consists of the following core components:
- Node: Computer within the system
- Transaction: Actual transaction of value, the smallest component of the Blockchain
- Block: It’s a data structure where transactions are stored in a Merkletree format.
- Chain: A sequence of blocks in a specific order.
- Miners: Specific nodes that perform the transaction and block validation
- Consensus: A mechanism through which networks reach the agreement
In a nutshell, here’s how a Blockchain works in six steps:
- Node submits the transaction in the network.
- Miners pick up the transaction and keep it in the memory pool.
- Miners add the transaction in the block.
- Miners submit the block and compete in the network to find the hash of the block (if consensus is based on proof of work system).
- Once the proper hash is found, the block is submitted to the network.
- Every other node verifies the hash, and if 51% of the nodes verify and find the hash to be correct, the network reaches consensus, and the block becomes immutable.
Let’s understand each component in brief.
Node
Each participant in the network is called a node. A node is a computer running the software required to join the Blockchain network.
It does require an internet connection to join and participate in the network. It can be a simple computer laptop or a huge data center.
In a public Blockchain, anyone can become a node and join the network. The number of nodes is important to make the system more secure and hard to attack.
Transaction
The transaction is the basic building block of the Blockchain. It is generated by the node and submitted in the chain, which is later picked up by the Miner and added to the block.
The transaction consists of the following information:
- ID (hash)
- Address (hash)
- Receiver (hash)
- Amount – Amount to send in crypto
- Fees – Fees to send the transaction
- Signed hash – Hash generated by the sender
There is little more information depending on the cryptocurrency, but the above-mentioned information is mandatory.
Did you notice that there is no user information stored? This is because Blockchain promises anonymity, so no information about the sender is stored except their address, which is again a hash.
Block
Block is a data structure that stores a bunch of transactions and submits them to the Blockchain for validation. If validation is successful, the block becomes immutable.
The Miner Node generates blocks. Miner Node picks up transactions from the memory pool and generates a block. This block is also called “Candidate block.”
Every block consists of the following:
- Block header: Contains version, last block, time, and target
- Nonce: Number to consider for hash generation
- Transactions: List of transactions in a Merkletree format
Block header consists of critical information such as version number, last block hash, timestamp, target number, and so on.
The block is added in the chain by hashing the block header and hoping that data is less than the target number.
The target number is decided using the difficulty number. A Difficulty is a number that decides the time taken by the miner to mine the block. It Should be around ~10 minutes on the Bitcoin network.
A nonce is a number that is used by the miner to generate the hash to meet the target number. The Nonce is incremented by the miner to meet the required target value.
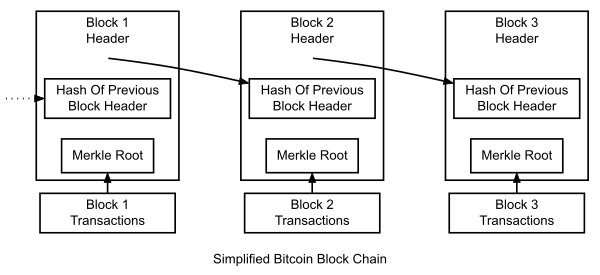
Once the hash is found, the block is mined and submitted to the
chain. Each block is linked with the previous block, forming the chain as seen in the following image:
Let’s proceed to the next component.
Chain
The chain is the blocks linked together using cryptography and
shared across every node. Each node maintains the latest copy of the chain, forming the network of strong, reliable, and consistent nodes.
The chain consists of blocks. Blocks contain transactions, as you saw earlier. Each transaction is associated with the account, forming the ledger. Using the chain, one can determine the ledger information of the particular address and verify the transactions.
Since the chain is distributed across the network, there is no chance of fraud. If someone tries to add a false block from their machine, the network will verify and reject the block. To take over the network, one must have 51% control of the node (Hashing/Computing power of the node) in the network.
It is also called a 51% attack.
51% attack is the distributed attack in which attackers try to control the Blockchain network by infecting and controlling hashing power of 51% of the nodes. It’s nearly impossible for the network, such as Bitcoin, but it can be implemented for smaller networks.
The chain is shared across the nodes in the network in the following steps:
- New transactions are broadcast to all nodes
- Each node collects new transactions into a block
- Each node works on finding a difficult proof-of-work for its block.
- When a node finds proof-of-work, it broadcasts the block to all nodes
- Nodes accept the block only if all transactions in it are valid and not already spent
- Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash
These steps are mostly the same for the majority of the proof of the work-based system.
The chain is stored in the binary format on the nodes. Depending on the operating system and chain network, it is stored at the following location by default, and we are taking the Bitcoin chain as an example:
Linux
/home/[username]/.bitcoin/blocks/
Windows
C:\Users\[username]\AppData\Roaming\Bitcoin\
Mac
~/Library/Application Support/Bitcoin/
You can, of course, store it at different locations based on the chain configuration.
Let’s proceed to one of the most important components of any
chain—Miners.
Miners
Miners are the nodes that perform the process to add a new block in the chain, adding the transactions sent by the user.
Miners do this process by performing a deep level of hash calculations that takes around 10 minutes in the case of Bitcoin.
This calculation costs a lot of computing power, so it is required to pay the miners to run the operation in the surplus profit. Every time a miner performs a successful block insertion in the chain, the system rewards them with an incentive. In the case of Bitcoin, it is 12.5 Bitcoin per successful block at the time of writing this article.
So, how does mining work?
The mining process begins with building a new candidate block by picking up the transactions from the memory pool.
The candidate block contains the block header. Miners try to calculate the hash bypassing the block header to the SHA256 function.
SHA256 is the hash function used to generate a hash
based on the input.
The hash returned should be lower than the target value defined by the system at the moment. If not, the miner increments the Nonce and calculates the hash again. This process continues until the correct hash is found. Hash is a CPU-intensive process, so most miners use advanced CPUs to perform this job.
The mining process is energy dominant, so it requires lots of electricity to perform the hash calculations. Miners also collect the transaction fee provided in each transaction, plus the mining reward generated by the system
Let’s learn how consensus is being achieved in the Blockchain
network.
Consensus
The consensus is the set of rules agreed by all parties of the network. There are three types of consensus algorithms used by the Blockchain networks.
- Proof of work
- Proof of stake
- Byzantine fault tolerance
Proof of work is the original consensus mechanism created by Satoshi Nakamoto for the Bitcoin cryptocurrency. Let’s understand both of them in detail.
Proof of Work
Proof of work is a consensus mechanism in which one has to produce data that is difficult to generate but easy to verify.
Bitcoin uses proof of work and asks miners to generate the hash, which is less than the target number. In Bitcoin, the miner has to produce a hash that starts with certain 0s. For example, if the target is 10, a miner has to produce hash starts with beginning with 0s that are less than 10.
It sounds simple, but it’s extremely difficult to generate using the SHA-256 function. Once a hash that satisfies the target is generated, all the others can verify using the target that was used to generate the hash. So, it’s easy to verify but hard to generate.
Why is it so tough to generate?
To prevent spam and denial of service attacks, proof of work asks miners to invest a ton of money to build an infrastructure to perform mining, and they are rewarded by the system.
This difficulty also ensures that the false transaction does not flood the system because it will take lots of time and money to flood the system with the bad transaction; instead, one will mine and earn some good money!
Proof of Stake
Proof of work is a solid consensus mechanism, but it consumes a
lot of computing power and energy. The energy cost to generate my blocks is so high that one can power an entire city with that energy.
Proof of work is faced with scaling issues. To solve these scaling issues, engineers across the world agreed to another form of consensus that is called Proof of Stake (POS).
In proof of work, when the block is about to be mined, every miner in the network tries to generate the hash to earn the reward. Ultimately, only one miner among thousands will get the hash and the reward, which, in turn, wastes the efforts of other miners.
In proof of stake, the miner/validator is chosen based on various stakes such as random, several blocks mined, and so on. So, the network chooses the miner and asks them to mine the block, giving everyone a fair chance plus saving the effort of other miners.
In proof of stake, the stake could be money, ranking, or stake itself. When a miner tries to cheat and add a bad/corrupted block in the network, the stake is slashed, or a penalty is charged against the miner.
So, how is the miner selected in proof of stake?
In general, it can be done randomly. The system picks up a random miner from the network and assigns them the block.
The network can assign a formula using which it can decide the
miner when a new block is ready to mine.
Proof of stake is simple and saves lots of computational effort. Ethereum, the second most popular cryptocurrency in the world, is going to make a switch to proof of stake-based consensus from proof of work, which is their current consensus mechanism.
Let’s understand another popular consensus mechanism, i.e.
Byzantine fault tolerance.
Byzantine Fault Tolerance
Byzantine Fault Tolerance (BFT) is a consensus mechanism in a distributed system, wherein consensus is reached even if the nodes in the network fail to respond or respond with incorrect information.
BFT ensures that the system is up and running and performing its function even if the network is under attack or some technical issues occurred.
So far, we have studied the Blockchain and its components. These concepts must be studied by the individual who wants to learn Blockchain and cryptocurrency.
This article is referred from the Book called Building decentralized blockchain applications.Consider a purchase if you like our content. (PS: I am author of this book)