New to Rust? Grab our free Rust for Beginners eBook Get it free →
Leveraging Kubernetes Admission Controllers for Enhanced Security Using ARMO
Nowadays, many organizations are switching from conventional development and deployment methods to microservices that operate in containerized environments. After all, these microservices are scalable and simple to set up. And when it comes to the management of all of these services, most organizations use a platform called Kubernetes.
Kubernetes is a popular open-source platform that automates container orchestration and is known as the most common platform. It assists in deploying, scaling, and managing containerized applications. Kubernetes’ capacity to deliver autonomous scaling and self-healing capabilities are two of its most important selling points, and they’ve helped it become the platform of choice for many businesses.
Kubernetes has several built-in capabilities that can assist in making its clusters more secure. Therefore, Kubernetes security is an essential component of the platform as a whole. One of these capabilities is the utilization of admission controllers, which are used to validate and alter incoming requests to the Kubernetes API server. These requests are sent to the Kubernetes API server.
The usage of admission controllers enables the enforcement of security policies, such as the requirement of particular labels to be placed on pods or the denial of requests that do not satisfy certain security requirements.
Understanding Kubernetes Admission Controllers
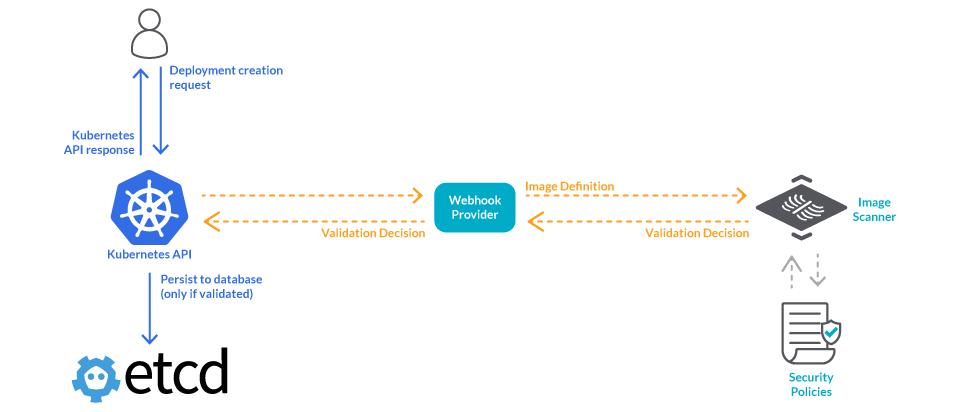
Admission controllers are a feature of Kubernetes that are used to validate and modify incoming requests that are sent to the Kubernetes API server to be processed further. These admission controllers are executed before the requested operation is performed, and as a result, they can be used to enforce security policies. For example, they can be used to determine whether the deployment of a pod requires a particular label or to deny requests that do not attempt to perform certain sensitive actions that are not allowed.
Kubernetes comes with a number of built-in admission controllers, one of which is called the NamespaceLifecycle. This controller is utilized to validate that a namespace is in the appropriate state for an operation that has been requested. For example, this controller will check to see if a namespace is active before a new object is created within it.
The admission controllers of an organization can also be tailored to the organization’s particular requirements if so desired. These Custom admission controllers can be implemented as webhooks, which are external HTTP servers that can be used to validate and mutate incoming requests.
For example, organizations can enforce a policy that every pod created with the latest image should have the latest label. Webhooks are “external HTTP servers that can be used to validate and mutate incoming requests”.
In addition to verifying and modifying requests, admission controllers can also be used to append additional information to a request. However, this functionality is not required. For instance, an admission controller might programmatically apply labels to pods according to the namespaces those pods belong to.
Types of Admission Controllers and Their Specific Use Cases
Kubernetes makes available a wide variety of admission controllers, each of which may be configured to carry out a particular function or adhere to a certain policy. Let’s look at some of the more popular Kubernetes Admission controllers and the policies they impose.
NamespaceLifecycle
The NamespaceLifecycle admission controller is in charge of regulating the process by which users create new namespaces and delete existing ones. It guarantees that namespaces are established with the appropriate permissions and labels, as well as enforcing policies, such as who is authorized to create or delete namespaces. This admission controller contributes to the management of the lifetime of namespaces, which helps to ensure that the cluster always has a consistent state.
PodSecurityPolicy
The PodSecurityPolicy admission controller is responsible for monitoring and enforcing pod security regulations. Before it is created, it performs a check on the pod’s specifications to make certain that the newly deployed pod satisfies the necessary security conditions. These conditions may include running with a non-root user or an unprivileged user, making use of a particular security context, or making use of a particular set of host volumes. By ensuring that all pods comply to a predetermined set of security regulations, the PodSecurityPolicy admission controller contributes to the maintenance of the cluster’s level of safety and security.
Managing K8s Security Compliance with Armo Platform
Since Kubernetes clusters are susceptible to a wide variety of security risks, it is critical to put security safeguards in place to satisfy various regulatory mandates for security compliance. Enforcing RBAC and network segmentation are two of the general security and compliance requirements that must be met, in addition to adhering to a few industry standards. Because of this, maintaining security and compliance within Kubernetes clusters is of utmost importance.
Enforcing security and compliance on the whole network or cluster requires scanning the entire cluster with automated tools such as Armo Platform.
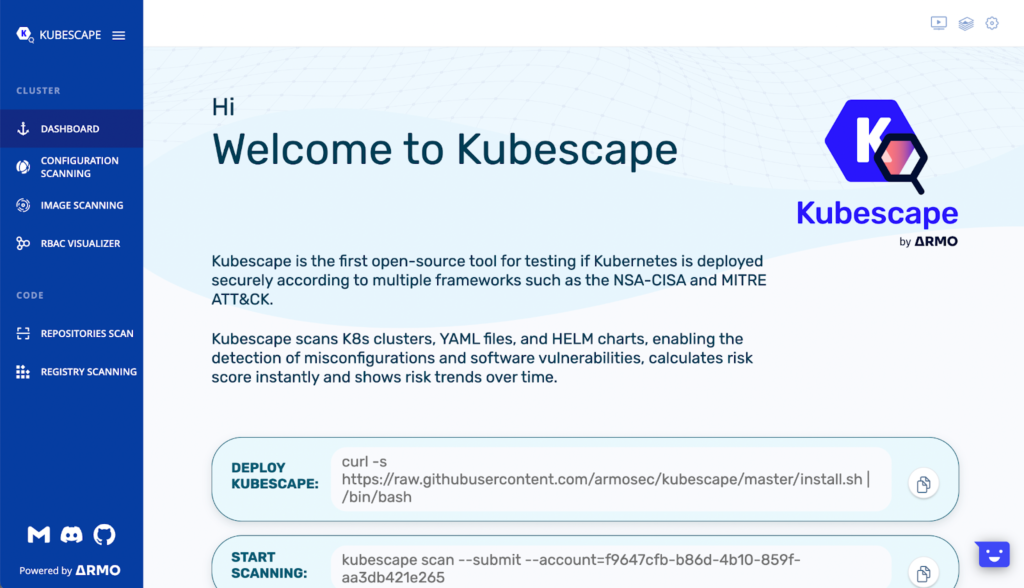
Armo uses the Kubescape project, which does a scan of all of your Kubernetes and IaC components in a single location, then transfers the results to the cloud platform so that everything can be correctly seen within a dashboard.
You can get Kubescape up and running with a single command:
curl -s https://raw.githubusercontent.com/kubescape/kubescape/master/install.sh | /bin/bash
This tool supports the broadest range of industry-leading frameworks, including CIS, NSA, MITRE, and more. Additionally, it gives you the flexibility to add your own custom framework within it, and you can scan your entire cluster using that particular framework as well. You can visualize all of the results on a single platform, which features hundreds of controls unique to K8s, and you can save the history of any past scans.
You can execute the following command to carry out the scanning by making use of the frameworks pre-defined in the tool.
kubescape scan framework <framework name such as mitre, nsa>
It will scan the whole cluster for controls based on the MITRE framework.

You can use this easy command if you wish to conduct scans for all of the preventive controls that have already been defined in Armo.
kubescape scan –enable-host-scan –verbose
After you have executed the command, the host scan will be performed, and it will mark all the controls that have failed or those with which the cluster is not compliant. The execution of this command will upload all the results to the Armo cloud where you will be able to view them and take appropriate action.
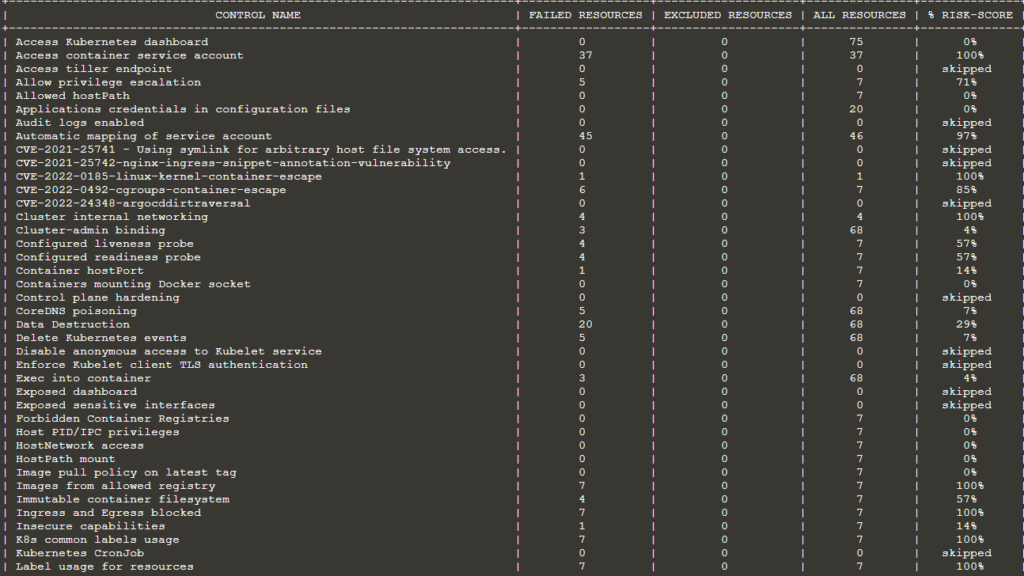
You can implement or enforce RBAC with proper visualization by doing things like applying filters to users or roles and determining which users have which types of controls. This is because when you scan the entire cluster, it will also collect data regarding the RBAC controls. Therefore, you will have complete information regarding the controls, security, and compliance in a single location.
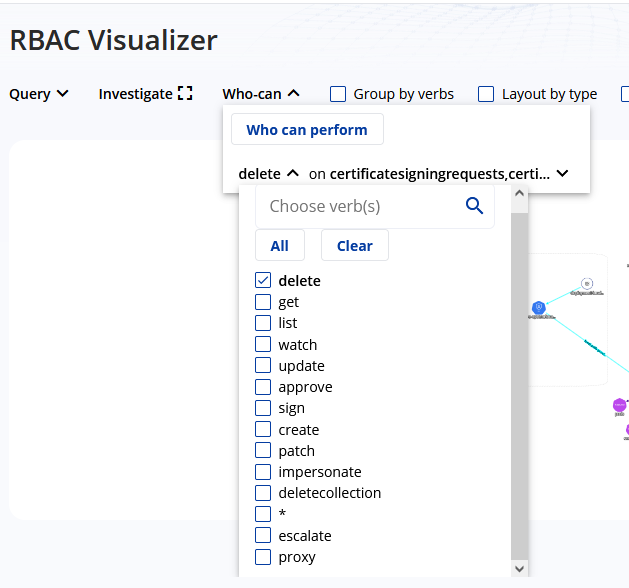
It is quite helpful for organizations to use automated tools for managing security and compliance within Kubernetes clusters. The tools automate compliance checks and reduce the manual effort required to maintain compliance, speeding up the process and reducing your efforts considerably. In addition, automated tools ensure that compliance policies are uniformly enforced across the whole cluster. This reduces the chance of compliance violations since the tools can scan the cluster easily and quickly by running a simple command. Thanks to this feature, it becomes much simpler for teams to guarantee that their Kubernetes clusters comply with all applicable norms and standards.
Conclusion
The security model for Kubernetes clusters relies heavily on admission controllers as a critical component. They ensure compliance with policies and examine the resources’ specs before allowing them to join a cluster. Enforcing rules and constraints on what kinds of resources can be generated and managed within the cluster helps ensure the cluster’s security and compliance with regulations.
Organizations can utilize automated technologies such as Armo, which can scan clusters utilizing many of the popular frameworks, like MITRE, NSA, and others. By implementing admission controllers and automated tools, businesses can streamline the process of assuring compliance and security in their Kubernetes clusters, thereby lowering the likelihood of security incidents and enhancing their cluster’s overall security posture.


